Ransomware gangs have become a significant threat in the digital age, wreaking havoc on businesses, governments, and individuals alike. These cybercriminals operate with sophistication, targeting specific organizations and systems to maximize their profits. In this blog post, we’ll dive into the world of ransomware gangs, explore their top players, explain what they target, and provide real-world examples and use cases of how they exploit their targets.
What is Ransomware?
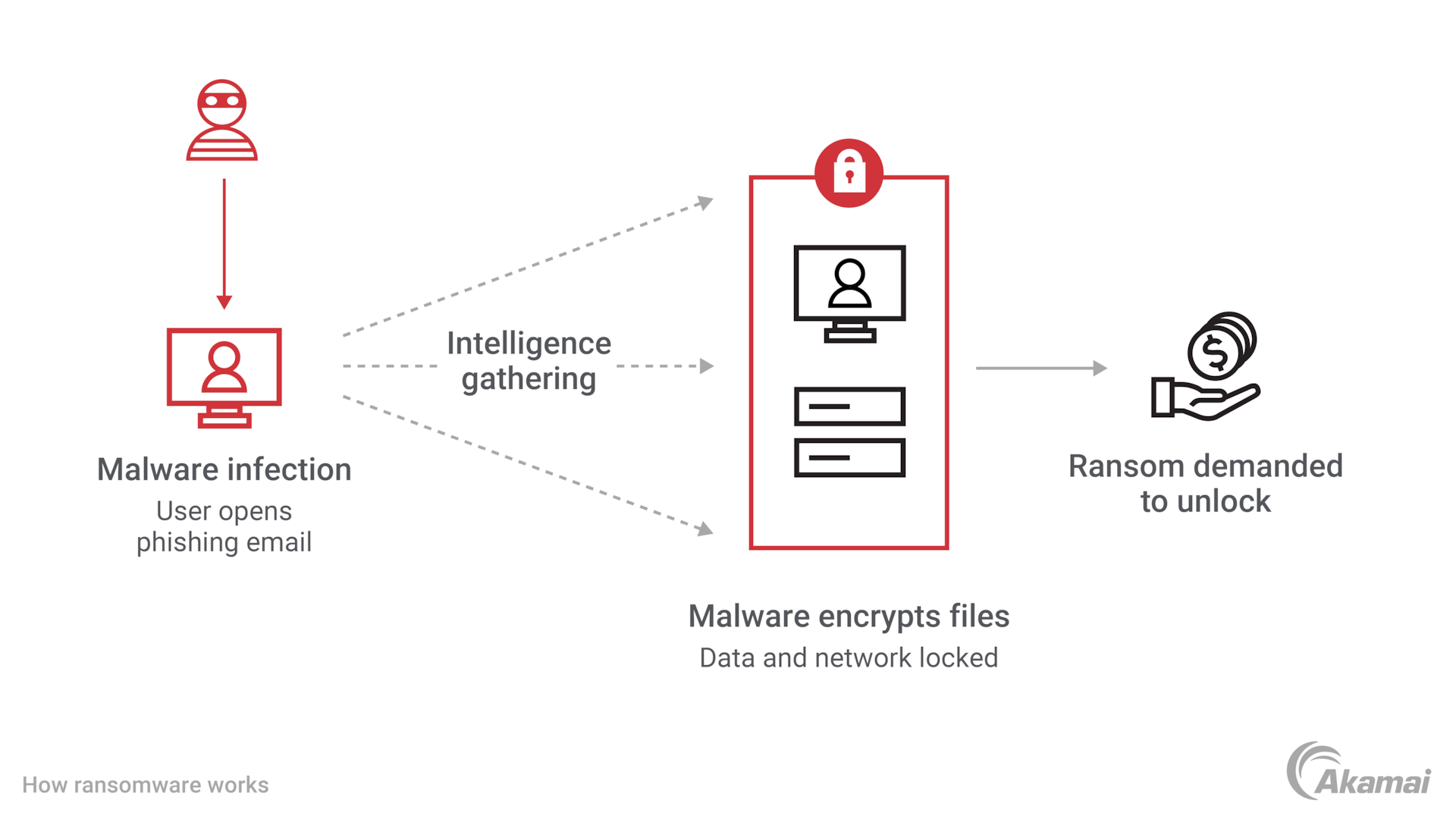
Ransomware is a type of malicious software (malware) that encrypts a victim’s data, rendering it inaccessible until a ransom is paid, typically in cryptocurrency like Monero. These attacks often involve stealing sensitive data and threatening to leak it unless demands are met. Ransomware gangs are organized groups behind these attacks, operating like businesses with clear strategies and hierarchies.
Top Ransomware Gangs in 2025
While the ransomware landscape evolves rapidly, several gangs have consistently stood out due to their scale, impact, and sophistication. Here are some of the most notorious ransomware gangs active in 2025, based on their activity and impact:
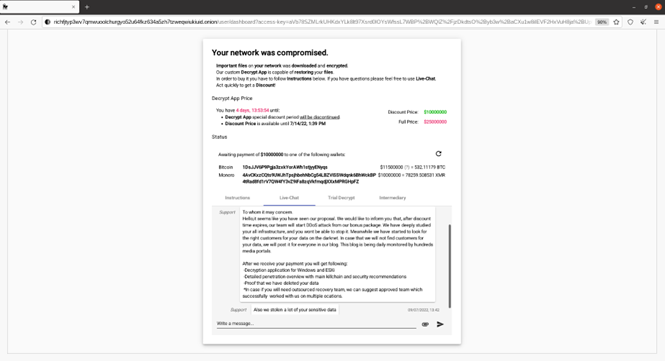
- LockBit LockBit is one of the most prolific ransomware-as-a-service (RaaS) groups. They provide their malware to affiliates who carry out attacks, making them highly scalable. Known for their aggressive tactics, LockBit has targeted a wide range of industries, from healthcare to manufacturing. Their double-extortion strategy—encrypting data and threatening to leak it—has made them particularly dangerous.
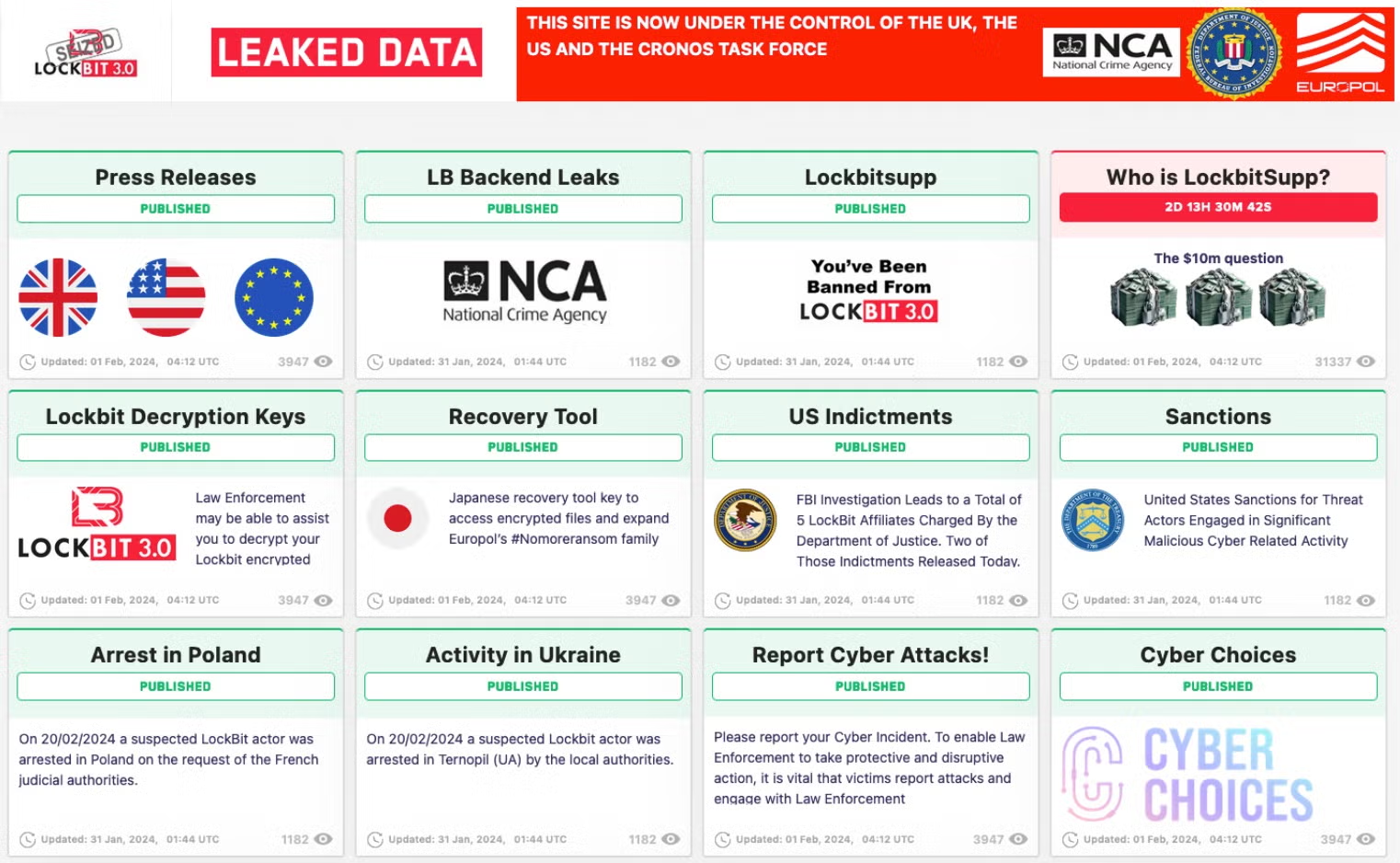
- ALPHV (BlackCat) ALPHV, also known as BlackCat, is known for its advanced coding and use of Rust programming language, which makes their ransomware harder to detect. They target large enterprises and critical infrastructure, often demanding multimillion-dollar ransoms. Their focus on high-value targets has cemented their reputation as a top-tier gang.
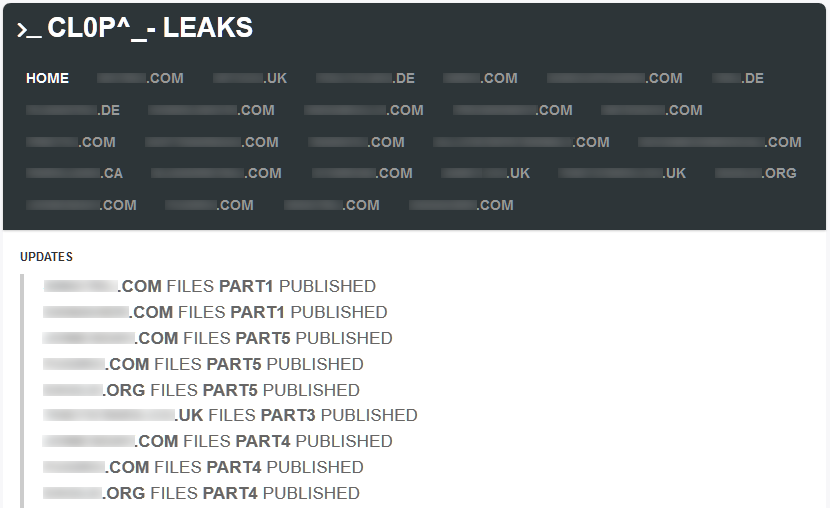
- Cl0p (Clop) Cl0p has gained notoriety for exploiting vulnerabilities in widely used software, such as file transfer tools. They focus on data theft and extortion, often bypassing encryption altogether. Cl0p has targeted organizations in finance, retail, and technology, leveraging stolen data to pressure victims into paying.
-
Conti (and its successors) Conti was a dominant player until its dissolution in 2022, but its affiliates have splintered into new groups like Black Basta and Royal. These successors continue Conti’s aggressive tactics, targeting healthcare, education, and government sectors. Their attacks often disrupt critical services, increasing pressure on victims to pay.
-
REvil (Sodinokibi) Though less active in recent years, REvil’s legacy persists through its affiliates and copycats. Known for high-profile attacks on corporations and supply chains, REvil’s tactics include massive ransom demands and public shaming of victims via leak sites.
What Do Ransomware Gangs Target?
Ransomware gangs are strategic in their choice of targets, focusing on entities that are likely to pay due to the critical nature of their operations or the sensitivity of their data. Here’s a breakdown of their primary targets, why they’re chosen, and examples of real-world attacks:
- Critical Infrastructure

Examples: Hospitals, power grids, water treatment facilities, and transportation systems.
Why They’re Targeted: Disrupting critical infrastructure can have life-or-death consequences, increasing the likelihood of ransom payment. For example, a hospital unable to access patient records may pay to restore systems quickly.
Case Study: In 2021, the Colonial Pipeline attack by DarkSide disrupted fuel supplies across the U.S., causing widespread panic and shortages. The gang exploited a compromised VPN account to infiltrate the pipeline’s network, encrypting critical systems.
Exploit Use Case: DarkSide used a stolen password from a phishing attack to access the VPN, highlighting the importance of multi-factor authentication (MFA).
- Large Enterprises and Corporations
Examples: Multinational companies, financial institutions, and tech firms.
Why They’re Targeted: Large organizations have deep pockets and often store sensitive data, such as customer information or intellectual property. The financial and reputational damage of a data breach makes them prime targets.
Case Study: In 2023, LockBit targeted a major U.S. financial institution, encrypting customer data and threatening to leak it. The attack began with a spear-phishing email targeting an executive.
Exploit Use Case: LockBit exploited a misconfigured cloud server to gain initial access, then used lateral movement to deploy ransomware across the network.
- Small and Medium-Sized Businesses (SMBs)
Examples: Local businesses, law firms, and retail chains.
Why They’re Targeted: SMBs often lack robust cybersecurity, making them easy prey. They may also be less prepared to recover from an attack, increasing the chances of payment.
Case Study: In 2022, Cl0p attacked a regional law firm via a vulnerable file transfer tool, stealing sensitive client data and demanding a ransom to prevent its release.
Exploit Use Case: Cl0p exploited a zero-day vulnerability in the file transfer software, emphasizing the need for timely software updates.
- Government and Public Sector
Examples: Municipal governments, schools, and public agencies.
Why They’re Targeted: Public sector organizations often have outdated IT systems and limited budgets for cybersecurity. Attacks on schools or government offices can disrupt public services, creating pressure to pay.
Case Study: Conti’s 2021 attack on Ireland’s Health Service Executive (HSE) crippled healthcare services, delaying patient care. The gang gained access through a phishing email containing a malicious Excel file.
Exploit Use Case: Conti used a macro-enabled Excel file to deliver malware, exploiting lax email security filters in the HSE’s network.
- Supply Chains and Third-Party Vendors
Examples: Logistics companies, software providers, and cloud service vendors.
Why They’re Targeted: Compromising a single vendor can give gangs access to multiple organizations. Supply chain attacks amplify the impact, as seen in the 2020 SolarWinds attack.
Case Study: The 2020 SolarWinds attack, attributed to a state-sponsored group but emulated by ransomware gangs like REvil, compromised multiple organizations by injecting malicious code into software updates.
Exploit Use Case: REvil affiliates exploited trusted software updates to distribute ransomware, underscoring the risks of unverified third-party software.
How Do Ransomware Gangs Operate?
Ransomware gangs operate like professional organizations, with specialized roles such as developers, negotiators, and penetration testers. They use a variety of tactics to infiltrate systems and maximize payouts:
-
Phishing and Social Engineering: Sending malicious emails or tricking employees into revealing credentials. For example, Conti’s HSE attack began with a phishing email targeting an employee.
-
Exploiting Vulnerabilities: Targeting unpatched software or misconfigured systems, like Cl0p’s zero-day exploits in file transfer tools.
-
RaaS Model: Many gangs, like LockBit, operate as RaaS, allowing affiliates to use their ransomware in exchange for a cut of the profits.
-
Dark Web Leak Sites: Gangs publish stolen data on dark web sites to pressure victims into paying, as seen with ALPHV’s data leaks.
-
Cryptocurrency Payments: Ransoms are typically demanded in Bitcoin or Monero for anonymity.

Why Are Ransomware Attacks So Effective?
Ransomware gangs succeed because they exploit human and technological weaknesses. Poor cybersecurity practices, such as weak passwords or unpatched systems, make it easier for them to gain access. For instance, the Colonial Pipeline attack exploited a lack of MFA, while Cl0p’s attacks leveraged unpatched software. Additionally, their use of double-extortion tactics increases the stakes for victims, who face not only data loss but also reputational damage. The rise of cryptocurrency has also made it easier for gangs to collect ransoms anonymously.
Protecting Against Ransomware
While ransomware gangs are formidable, organizations and individuals can take steps to reduce their risk:
-
Regular Backups: Maintain secure, offline backups to restore data without paying the ransom.
-
Patch Management: Keep software and systems updated to close vulnerabilities, as unpatched systems were key in Cl0p’s attacks.
-
Employee Training: Educate staff on recognizing phishing emails and suspicious links, which could have prevented Conti’s HSE attack.
-
Endpoint Security: Use antivirus software and firewalls to detect and block malware.
-
Multi-Factor Authentication (MFA): Implement MFA to prevent unauthorized access, as seen in the Colonial Pipeline case.
-
Incident Response Plan: Develop a plan to respond quickly to attacks and minimize damage.
Conclusion
Ransomware gangs like LockBit, ALPHV, Cl0p, Conti’s successors, and REvil are a growing threat, targeting critical infrastructure, corporations, SMBs, governments, and supply chains. Their sophisticated tactics, such as phishing, zero-day exploits, and supply chain attacks, make them formidable adversaries. By understanding who they are, what they target, and how they exploit vulnerabilities—through real-world examples like the Colonial Pipeline, HSE, and SolarWinds attacks—organizations can better prepare and protect themselves. Staying vigilant, investing in cybersecurity, and fostering a culture of awareness are key to staying one step ahead of these digital criminals.
Stay safe, and keep your systems secure!


